Executive summary
[See Appendix A for acronyms].
Buildings don’t perform off drawings; they perform in operation. Converging BMS[1] and IoT[2] turns BIM’s[3] design intent into a live, auditable operating layer—one that cuts energy and carbon, improves uptime for critical services, and strengthens cyber posture across the estate.
The foundation is resilient, brokered connectivity with secure outbound-only access, so telemetry and remote changes are reliable without exposing inbound services. It is important to treat this as digital infrastructure: with telemetry, control, and security on the same footing as finance or HR.
This paper applies CSL Group’s proven mission-critical connectivity expertise—honed across 3.5 million connected devices in fire, security, and critical infrastructure—to the emerging challenge of secure, resilient BMS-IoT convergence. We extend dual-path resilience, patented multi-network roaming, and zero-trust security principles from individual life-safety systems to entire building management ecosystems.
The outcome: A secure, resilient operating layer for buildings: live data, closed-loop control, and audit-ready evidence—scalable across your estate and future-proofed with resilient rSIM[4]/eUICC[5] options where appropriate.
Section Footnotes:
[1] Building Management System
[2] Internet of Things
[3] Building Information Modelling
[4] resilient SIM; multi-network SIM with dual-core architecture and automatic failover
[5] embedded UICC (eSIM) with remote profile management
Why is this important now?
- Tighter regulation and insurer expectations for segmentation, device identity, and evidence.
- Energy volatility plus electrification (EVs, heat pumps) driving operational change and integration.
- Estate-wide cyber risk converging onto building systems.
Architecture at a glance
- Connectivity & access: Dual-path (fixed + multi-network dual-core cellular) via private APN[1]/VPN[2] and mutual TLS[3]; no inbound pinholes[4].
- Brokered[5] by design: Standards-based broker (e.g., MQTT v5) with QoS[6], retained messages[7], and session expiry[8] for reliable delivery.
- Open & portable: IFC[9] for context, Project Haystack[10] tags for points, BACnet/SC where required—avoids lock-in.
- Operational proof: IPMVP-verified[11] energy savings, faster incident recovery (target ≤ 5 min under test), and auditable control.
Section Footnotes:
[1] Access Point Name (private mobile network gateway)
[2] Virtual Private Network
[3] Transport Layer Security
[4] A pinhole is a specific opening in a firewall that allows inbound network traffic to reach device or system inside the protected network.
[5] Brokered connectivity is a secure, outbound-only model where devices connect to a central message broker over mutual TLS. The broker enforces identity and authorisation, then routes telemetry and control messages. This removes inbound firewall holes and provides a single point to audit access across the estate.
[6] Quality of Service
[7] MQTT feature where the broker stores the most recent value for each topic, enabling new subscribers, (i.e. analytics tools, dashboards), to instantly see current building state rather than waiting for the next sensor update – critical for fast diagnosis and startup synchronisation.
[8] Session Expiry defines how long the broker ‘holds’ a device’s place and queued messages during temporary network loss. (e.g. cellular handoff, brief outage). Prevents message loss during short disconnections while automatically cleaning up abandoned sessions from permanently offline devices.
[9] Industry Foundation Classes are open, international standards for exchanging building and facility information between different software applications.
[10] Project Haystack: Open-source semantic data model that uses standardised tags (e.g. site, equip, point, temp, sensor) to describe building equipment and IoT data in a vendor-neutral way. Enabling analytics, digital twins, and management systems to automatically understand and process operational data without custom integration for each service type.
[11] IPMVP-verified: Savings measured using the International Performance Measurement and Verification Protocol, which defines rigorous baseline-vs-actual comparison methods. Provides investment grade certainty for business cases, ESG disclosures, and energy performance contracts by eliminating disputes over whether claimed savings are real.
Applying mission-critical connectivity to BMS
If it wouldn’t fly for life-safety, it isn’t good enough for building operations.
CSL Group has pioneered resilient connectivity for life-critical systems—fire alarm panels, security systems, critical infrastructure—where a single connectivity failure can mean loss of life or catastrophic asset damage. Our dual-path signalling solutions keep over 3.5 million devices online 24/7 in environments where downtime isn’t just inconvenient—it’s unacceptable.
The convergence challenge: As buildings evolve from isolated automation systems to connected IoT ecosystems, they face the same resilience, security, and availability demands we’ve solved in the alarm and critical infrastructure sectors—but at vastly larger scale and complexity. Traditional BMS vendors approach this as a connectivity upgrade; we recognise it as a mission-critical systems integration challenge.
This paper demonstrates how to extend proven principles—dual-path resilience, cellular failover with patented roaming technology[1], zero-trust architecture, and proactive fault management—from individual alarm panels to entire building management infrastructures.
Where some BMS vendors ask, “how do we add IoT capabilities?” CSL Group asks, “how do we keep mission-critical systems operational when networks fail, security is compromised, or infrastructure comes under attack?”
The result is an architecture that doesn’t just enable smart building features—it ensures they operate with the same reliability and security enterprises demand from life-safety systems.
Section Footnotes:
[1] rSIM: CSL Group’s patented multi-network, dual-core roaming technology that automatically switches between cellular carriers when signal quality degrades or networks fail—proven in life-critical and critical infrastructure applications.
What this paper covers next
1) Value levers & KPIs, 2) Design principles and acceptance criteria, 3) Security and assurance models, 4) Operating models and roadmap, 5) FAQs
From BIM to continuous performance
BIM remains the design truth that buildings were constructed to operate to, but BMS–IoT convergence maps live points and events onto that model—using IFC for context and Project Haystack for tags—so the “digital twin” becomes a truly operating twin. One that optimises via analytics and automation, orchestrates work orders, evidences compliance, and learns from operational data.
The value levers & board‑level KPIs for implementing IoT in BMS systems
- Energy & carbon savings: kWh/m²; demand‑response revenue; verified savings (IPMVP) [E].
- System uptime & resilience improvements: MTTD and MTTR for BMS paths and critical assets (e.g. target ≤ 5 min under test).
- Heightened cyber posture: i.e. % of assets using mutual TLS with short‑lived certificates; network segmentation coverage across OT zones[1].
- Costs‑of‑servicing building systems: remote fix rate; truck‑roll avoidance; MTTDiag (Mean Time to Diagnose).
- User experiences:e. % time IAQ[2] within target band; comfort complaints per 1,000 occupants.
- i.e. (CFO: OpEx ↓, CIO/CISO: risk ↓, FM[3]: uptime ↑).
Section Footnotes:
[1] OT zones: Network segmentation approach that separates Operational Technology systems (HVAC, lighting, access-control, fire-life safety) into isolated zones based on criticality and trust requirements. I.e. Prevents a compromised HVAC system from accessing life-safety controls and keeps building systems separate from corporate IT networks.
[2] Indoor Air Quality
[3] Facilities Management
What good looks like (design principles → acceptance)
Smart features don’t survive brittle networks—so we design for field-failure first.
- Secure‑by‑design: All device‑to‑broker links must use mutual TLS with automated certificate rotation; no inbound pin‑holes.
- Open & portable: Point tagging must use Project Haystack; context mapped in IFC; telemetry via MQTT v5 with QoS/retained messages; automation via BACnet/SC where required [A] [B].
- Secure & resilient connectivity: Dual-path (fixed + multi-network dual-core cellular via rSIM), private APN/VPN, mutual TLS, outbound-only broker [F].
- Brokered access: Outbound‑only via secure brokers; time-boxed, audited sessions for integrators.
- Observability: Estate‑wide health metrics, signal and usage telemetry standards, and loss‑of‑comms alerts and mitigation.
Security & assurance
- Frameworks: apply connected-places security principles (UK) or equivalent national guidance (e.g., NIST CSF[1]) together with IEC 62443 for roles, zones/conduits, and supplier responsibilities [C]. For EN 54-21[2] and other regulated alarms, BMS–IoT augments monitoring only; it never replaces certified signalling paths.
- Suppliers should provide evidence of IEC 62443 compliance (or a time‑bound alignment roadmap) for OT‑facing components.
- Cadence & ownership: Quarterly tabletop exercises; annual ‘red‑team’ of BMS gateways; defined ownership for segmentation, PKI[3], and incident drills.
Section Footnotes:
[1] National Institute of Standards and Technology Cybersecurity Framework
[2] EN 54-21: European standard for alarm transmission systems and equipment used to transmit fire alarm and fault signals from fire detection and fire alarm systems to an alarm receiving centre
[3] PKI (Public Key Infrastructure): A framework of encryption and cybersecurity technologies that uses digital certificates and cryptographic keys to secure communications and authenticate devices. In this context, PKI ensures that only authorised IoT devices can connect to the BMS network.
Operating models
- Outcomes not devices: measure energy, uptime, and risk—not device counts.
- Data product: treat building telemetry as a governed product with SLAs and owners.
- Service wrapper: 24/7 UK‑based monitoring, 90‑day certificate rotation, quarterly incident drills, and KPI reviews as standard operations. Retention policy: raw 13 months, features 36 months; named data owner; PII[1] screening if occupancy/IAQ links to people systems.
Section Footnotes:
[1] PII (Personally Identifiable Information): Data that identifies or can be linked to specific individuals. In BMS-IoT convergence, PII concerns arise from access control logs (badge swipes, biometrics), occupancy sensors in personal workspaces, user-specific comfort settings, and maintenance audit trails. Organisations must ensure PII handling complies with GDPR (EU), CCPA (California), UK DPA 2018, or applicable jurisdictions, including data minimisation, encryption at rest and in transit, and defined retention policies.
Some questions to ask teams:
- What % of our critical assets are observable and controllable securely today—and which sites are excluded?
- When was BMS connectivity failover last tested, and what was the measured time‑to‑recover?
- Can we rotate device certificates and switch connectivity profiles easily and at estate scale without site visits?
- What are our IPMVP‑verified energy/carbon savings this quarter, and where is the audit trail stored? [E]
- How do we integrate building performance data with ESG[1] reporting and carbon accounting systems?
Section Footnotes:
[1] ESG (Environmental, Social, and Governance): Framework for measuring organisational performance on sustainability (energy, emissions), social impact (workforce, safety), and governance (compliance, oversight). BMS data supports mandatory ESG reporting under EU CSRD and UK TCFD.
Appendix A - Definitions (quick reference)
- BIM — Building Information Modelling.
- BMS — Building Management System.
- IFC — Industry Foundation Classes (building context/geometry). An open ISO standard schema for Building Information Modelling (BIM), enabling vendor-neutral exchange of asset metadata, geometry, and relationships.
- Project Haystack — an open tagging model for building data points.
- MQTT v5 — lightweight pub/sub protocol (QoS, retained messages, session expiry) [A].
- BACnet/SC — Secure Connect extension of BACnet for secure automation over IP [B].
- eIM — eSIM IoT Manager; platform for eUICC profile orchestration.
- eUICC — embedded UICC (eSIM) with remote profile management [F].
- GSMA SGP.31/32 — eUICC IoT architecture and operations specifications [F].
- rSIM — resilient SIM; multi-network SIM with dual-core architecture, pre-loaded operator profiles, and automatic failover between network cores – eUICC compliant.
- IPMVP — International Performance Measurement and Verification Protocol [E].
- TLS/PKI — Transport Layer Security / Public Key Infrastructure.
- SIEM/SOAR — Security Information & Event Management / Security Orchestration, Automation & Response.
- EVCP — Electric Vehicle Charge Point.
- APN — Access Point Name (private mobile network gateway).
Appendix B: Reference Architecture — Dual-Path Resilient Connectivity with Secure Broker Pattern
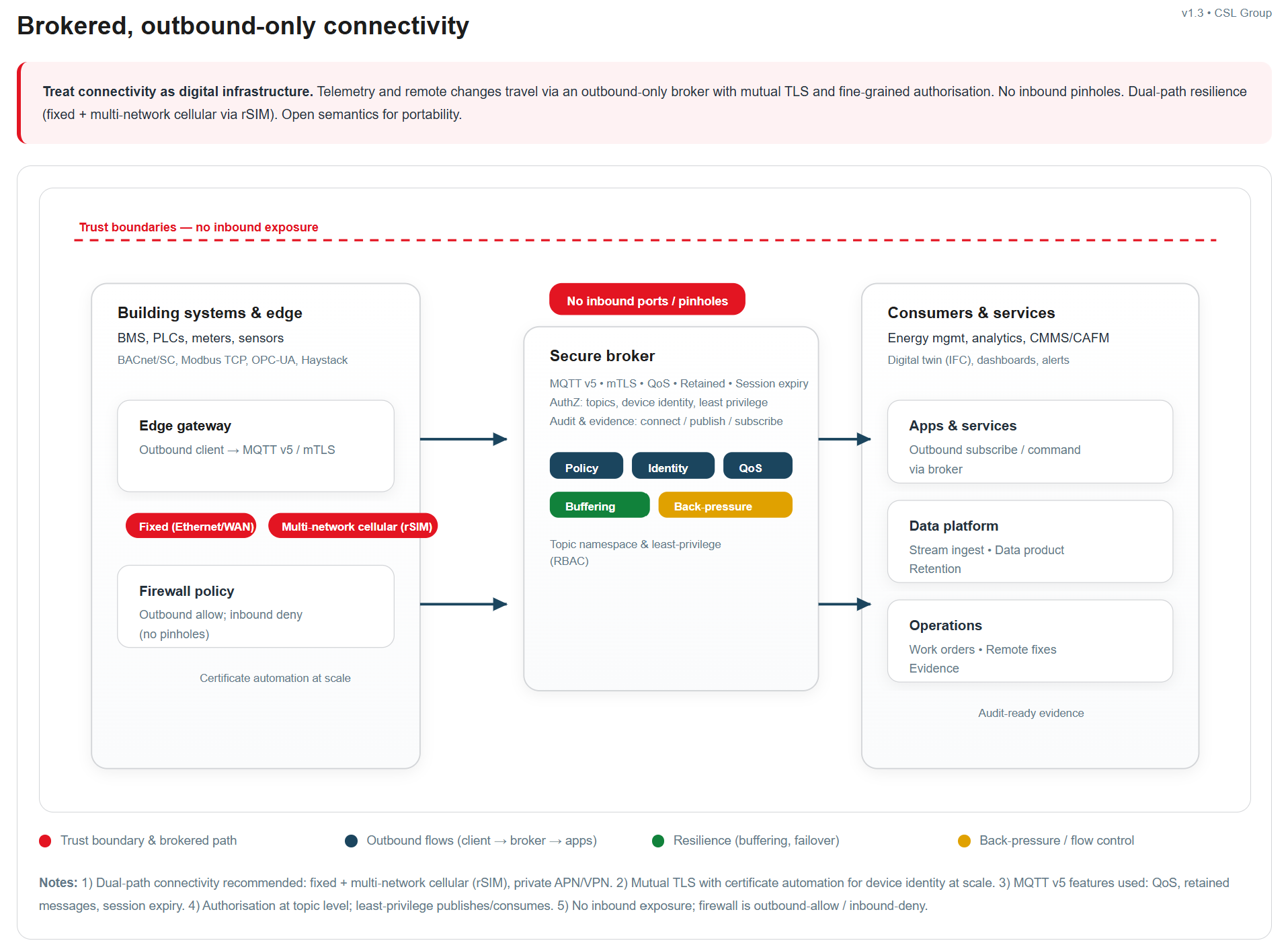
Note: Back pressure is a flow control mechanism that prevents system overload when a producer (sender) generates data faster than a consumer (receiver) can process it.
Appendix C - For Technical Leads
Interop & data
- Standard semantics: IFC + Project Haystack
- Transports: MQTT v5 (QoS, retained messages, session expiry) and BACnet/SC [A] [B]
Connectivity & access
Security is provided by the private APN/VPN tunnel plus mutual TLS. Deny inbound connections.
- rSIM / eUICC (GSMA SGP.31/32) options where appropriate; deployment route agreed case‑by‑case with critical connectivity partner; migration path towards SGP.32 as appropriate [F].
- Out‑of‑band management; active health checks (30–60s heartbeat; alert after ≥ 3 misses); loss‑of‑comms alerts.
Security & ops
- Zero‑trust, segmentation, mutual TLS, central PKI with automated rotation of device certificates (target 90 days); note that root/intermediate CAs[1] use longer lifetimes.
- SIEM/SOAR[2] integration; configuration drift monitoring with defined source‑of‑truth; incident runbooks.
KPIs & acceptance (examples)
- Failover detection + switchover time; path availability; end-to-end message success.
- Data integrity & timestamp accuracy; certificate hygiene; auditability.
- Opex[3]: fewer truck‑rolls, faster fixes, reduced energy waste, lower incident impact.
- Capex[4] deferment: better asset life through predictive maintenance; targeted replacements.
What your connectivity service should provide
- Resilient dual-core, multi‑network access for critical systems (BMS gateways, life‑safety visibility, lifts, EVCP[5]).
- rSIM resilience with eSIM/eUICC options and roadmaps aligned to SGP.31/32 (critical connectivity partner‑delivered), with a clear migration path to SGP.32 as appropriate. [F]
- Secure transport by design via private APNs and encrypted tunnels; device identity and segmentation baked in.
- Operational visibility: SIM/usage/signal telemetry, estate dashboards, proactive alerts.
- Assurance posture: ISO 27001 ISMS[6]; proven deployments across distributed critical estates.
Section Footnotes:
[1] Certificate Authority
[2] SIEM/SOAR (Security Information & Event Management / Security Orchestration, Automation & Response): Security platforms that collect, analyse, and respond to security events across IT/OT infrastructure.
[3] Operating Expenditure
[4] Capital Expenditure
[5] Electric Vehicle Charge Point
[6] Information Security Management System
BMS–IoT Convergence: Frequently Asked Questions (FAQ)
This FAQ addresses common questions and concerns from executives, facilities, IT/OT/security, procurement, and ESG/Sustainability teams regarding the BMS–IoT convergence programme.
Q1: Is this just another ‘IT project’ or will it really lower our energy costs and risk?
Expected impacts include 8–15% to 20% energy savings [D] in year one (IPMVP-verified where applied, subject to baseline controls and building typology), fewer engineer callouts via remote fixes, and faster incident recovery (target ≤ 5 min under test).
Q2: Do we lose control or lock-in by moving to open protocols?
No. Open standards (like MQTT, BACnet/SC, IFC, Project Haystack) prevent vendor lock-in and give you leverage in procurement. Your organisation keeps full control: you own the building data, broker connections are outbound-only for security, and critical connectivity partner-based SIM/eUICC orchestration ensures you can switch carriers/networks as needed [F].
Q3: Is this secure? What about cyber threats, especially with more cloud and cellular connections?
Yes—if zero-trust principles are applied. The architecture enforces outbound-only connections, mutual TLS (with short-lived certs and automated rotation), and segmentation per IEC 62443. No inbound firewall pinholes required, and all connectivity is private (APN/VPN). Continuous endpoint health checks and quarterly incident drills build cyber resilience.
Q4: How is failover assured? What about critical alarms (e.g., fire)?
Dual-path (fixed and multi-network cellular) connectivity is standard, with real-time health checks (30–60s heartbeat, rapid alert on three missed beats). BMS–IoT improves ‘monitoring and resilience’ but does not replace certified life-safety signalling (e.g., EN 54-21, hardwired alarms). For regulated alarms, integration adds observability, not primary signalling.
Q5: Why is CSL Group positioned to deliver this architecture versus traditional BMS or IT vendors?
CSL Group manages connectivity for over 3.5 million mission-critical devices—fire panels, security systems, critical infrastructure—where downtime can mean loss of life or catastrophic operational failure. We’ve spent decades perfecting capabilities that BMS convergence now requires:
- Dual-path resilience: Every CSL-connected device uses fixed broadband plus cellular backup with automatic failover—eliminating single points of failure that plague traditional BMS installations.
- Patented roaming technology: Our rSIM solutions automatically switch between cellular carriers when signal quality degrades, providing network redundancy that goes beyond single-carrier solutions.
- Cyber-secure OT connectivity: We’ve protected operational technology environments from IT network threats long before BMS-IoT convergence became an industry priority—understanding the unique security requirements where safety and availability outweigh traditional IT security models.
- Proactive fault management: CSL’s 24/7 monitoring detects connectivity degradation before customers experience outages—the same early-warning approach we now extend to comprehensive building systems.
- Regulatory compliance expertise: Our EN 54-21 compliant fire alarm transmission systems demonstrate our ability to meet stringent life-safety requirements—rigour we apply to all building infrastructure in this architecture.
The fundamental difference: Traditional BMS vendors are adding connectivity to automation systems. CSL Group is extending mission-critical connectivity principles—proven across millions of devices in the harshest failure conditions—to comprehensive building ecosystems. We don’t promise resilience; we’ve delivered it at scale for decades in applications where the cost of failure is measured in lives, not just operational disruption. This architecture isn’t experimental—it’s the application of battle-tested principles to an emerging market that now demands the same uncompromising reliability standards.
Q6: How is energy/carbon savings verified?
Savings are best verified using the IPMVP protocol—an internationally accepted standard for energy measurement and verification. ‘optimisation as usual’ isn’t enough—an IPMVP audit trail provides the evidence needed for credible Scope 1/2 (and potentially Scope 3[1]) carbon reporting [E].
Q7: Is this just for new builds, or can we retrofit?
Yes, existing buildings can and should be connected. The approach uses open protocols that work with legacy and modern BMS; most value is unlocked by connecting your existing estate, not waiting for new construction.
Q8: What does ‘operating twin’ mean—how is it different from BIM?
BIM captures your building ‘as designed’; BMS–IoT links BIM context to real-time data, creating a living ‘operating twin’ for continuous performance improvement, remote operations, analytics, and compliance evidence.
Q9: How do we ensure vendor accountability and futureproofing?
Contracts require open protocols, published semantics, and documented handover. Suppliers are obligated to align with ISO 27001 and IEC 62443, support remote SIM/eUICC management (GSMA SGP.31/32) where appropriate, and enable integration with your SIEM/SOAR and ERP[2] [F].
Note: SGP.31/32 adoption varies by operator and device. Where eUICC is selected and devices are compatible, we integrate closely with accredited eSIM IoT Manager (eIM)[3] providers and recommend a staged approach [F].
Section Footnotes:
[1] Scope 3: Indirect greenhouse gas emissions from sources not owned or directly controlled by the organisation, including upstream and downstream activities in the value chain (e.g., business travel, employee commuting, purchased goods and services, waste disposal, and use of sold products). Under the GHG Protocol, Scope 1 covers direct emissions, Scope 2 covers purchased energy, and Scope 3 covers all other indirect emissions.
[2] Enterprise Resource Planning
[3] eUICC Infrastructure Manager
Examples of BMS–IoT Convergence Plans
An example 12‑month roadmap (with exit criteria)
Q1 – Guardrails & discovery:
- Board mandate and risk appetite
- Asset & network inventory; quick‑wins backlog
- Security baseline (IEC 62443 aligned); procurement stance drafted
- Q1 exit: ≥ 95% inventory coverage; procurement pack approved; risk appetite agreed.
Q2 – Pilot with purpose (1–2 flagship buildings)
- Use‑cases: energy optimisation, predictive maintenance, remote secure access
- Measure: payback model, failover time, message success rate, incident drills
- Q2 exit: ≥ 8% energy reduction (IPMVP where applied); ≤ 5 min failover in drills; ≥ 99% end-to-end message success [E].
Q3 – Scale foundations
- ‘Golden gateway images’ (factory sealed, pre-hardened, tested and approved for deployment across all edge gateways in an estate); certificate automation; central broker and API layer
- eUICC profile strategy (critical connectivity partner‑delivered, operator/device dependent); observability dashboards; incident playbooks [F].
Q4 – Rollout & embed
- Expand to priority sites; integrate with CMMS/CAFM[1] & SIEM
- Quarterly KPI reviews; refresh compliance evidence; continuous tuning
- Q4 exit: ≥ 70% priority sites onboarded; CMMS/SIEM integrated; KPI reviews institutionalised.
Section Footnotes:
[1] Computerised Maintenance Management System / Computer-Aided Facility Management
References
[A] OASIS. MQTT Version 5.0 Specification — https://docs.oasis-open.org/mqtt/mqtt/v5.0/mqtt-v5.0.pdf [Accessed 22 Oct 2025]
[B] BACnet/SC (Secure Connect) overview — https://bacnetinternational.org/bacnetsc/ [Accessed 22 Oct 2025]
[C] UK NCSC: Connected Places Cyber Security Principles — https://www.ncsc.gov.uk/collection/connected-places [Accessed 22 Oct 2025]
[D] CIBSE Journal: Control strategy improvements can deliver 15–20% energy reductions — https://www.cibsejournal.com/technical/unlocking-the-secrets-of-the-black-box/ / Carbon Trust: Building energy management systems – A practical guide (CTG070). https://www.carbontrust.com/resources/building-energy-management-systems [Accessed 22 Oct 2025]
[E] Efficiency Valuation Organisation (EVO): IPMVP Protocol — https://evo-world.org/en/products-services-mainmenu-en/protocols/ipmvp [Accessed 22 Oct 2025]
[F] GSMA. “SGP.32 Remote SIM Provisioning for IoT — eUICC Profile Package, v1.1” (April 2024). Available: https://www.gsma.com/solutions-and-impact/technologies/esim/ [Accessed 22 Oct 2025]