Economic and Market Implications
The global smart building sector is poised for substantial growth, driven by the adoption of IoT-enabled management systems, rising energy efficiency demands, and increased sustainability awareness.
- Grand View Research estimates the market will grow from USD 126.58 billion in 2024 to USD 571.28 billion by 2030, reflecting a CAGR of 30.4% between 2025 and 2030.
- Fortune Business Insights projects growth from USD 117.4 billion in 2024 to USD 548.5 billion by 2032, with a CAGR of 21.2%. North America led the market in 2024, holding 40.63% of the global share.
- Global Market Insights forecasts an increase from USD 103 billion in 2024 to USD 827.7 billion by 2034, at a CAGR of 24.4%, citing the integration of 5G, AI, and advanced analytics as key drivers.
Despite variations in projections, analysts consistently anticipate strong growth over the next 5–7 years. In the UK and EU, the market is expected to expand from approximately USD 18.59 billion by 2030 to USD 26.4 billion by 2032.
Regulatory Foundations: UK and EU Approaches
Regulatory non-compliance in smart building initiatives carries substantial financial and operational risks. For instance:
- UK PSTI enforcement permits fines up to £10 million or 4% of global revenue—whichever is higher—and includes product recall authority.
- EU AI Act imposes fines up to €35 million or 7% of global revenue, with lower tiers at €15 million/3% and €7.5 million/1%.
- NIS2 Directive allows Member States to issue significant administrative penalties and binding compliance orders.
Given this regulatory landscape, providers of smart building technologies must balance innovation with strict adherence to cybersecurity, privacy, and ethical standards governing IoT and AI systems.
It is, therefore, highly important to fully understand the regulatory landscape when implementing IoT systems in smart building projects:
European Union: A Comprehensive Regulatory Framework:
The European Union has developed a more extensive regulatory ecosystem, including several key legislative instruments:
- General Data Protection Regulation (GDPR): Governs data privacy and protection.
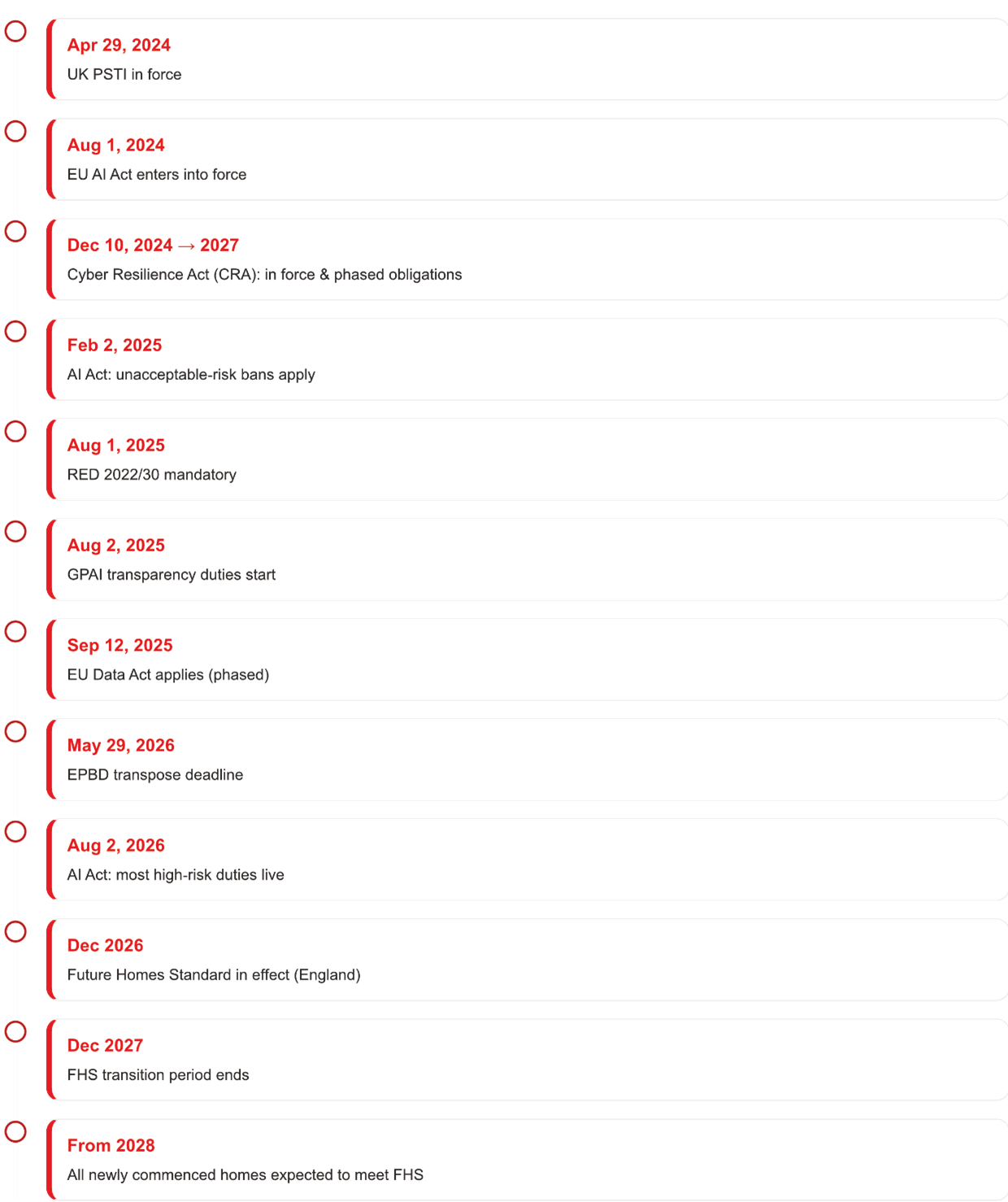
- AI Act: Provides governance for artificial intelligence systems. EU AI Act timeline:
- entered into force on 1 Aug 2024.
- bans on unacceptable‑risk systems applied from 2 Feb 2025.
- general‑purpose AI (GPAI) transparency duties began 2 Aug 2025.
- most high‑risk system obligations apply from 2 Aug 2026.
- Energy Performance of Buildings Directive (EPBD): Promotes smart technologies and energy efficiency.
- EPBD (recast) published 8 May 2024; entered into force 28 May 2024; transposition required by 29 May 2026.
- Network and Information Security (NIS2) Directive: cybersecurity obligations.
- Examples of entities that may be in scope include managed service providers supporting critical sectors, operators of large data centres/digital infrastructure, and building-technology SaaS providers above national size thresholds (scope depends on local transposition).
- NIS2 applies to ‘essential’ and ‘important’ entities per national transposition (deadline 17 Oct 2024). Many building owners/operators are only in scope if they meet sector/size criteria or act as managed service providers; check local implementing law.
Recent and Future impacting regulatory developments to note:
- Cyber Resilience Act (Regulation (EU) 2024/2847): in force since 10 Dec 2024; obligations phase in over three years (most by Dec 2027) for products with digital elements used in buildings.
- RED Cybersecurity Delegated Regulation (EU) 2022/30: mandatory since 1 Aug 2025 for internet‑connected radio equipment; addresses network protection, privacy, and anti‑fraud.
For buyers and operators, this set of rules defines the minimum bar for devices, the handling of personal data, and the reliability expected of AI‑enabled control systems.
United Kingdom: The Product Security and Telecommunications Infrastructure (PSTI) Act:
The UK has taken a pioneering step with the Product Security and Telecommunications Infrastructure (PSTI) Act, which came into full effect on 29 April 2024. This legislation addresses critical vulnerabilities in consumer-connected devices by mandating three fundamental security requirements:
- Unique Passwords: Manufacturers must ensure devices have unique passwords or allow users to create their own, eliminating universal default credentials.
- Vulnerability Reporting: Companies must provide clear instructions for consumers to report potential security issues.
- Security Update Transparency: Manufacturers must disclose the minimum period during which security updates will be available.
Scope note: PSTI targets consumer connectable products; some professional/BMS devices may fall outside unless consumer-facing or otherwise in scope.
What each law does; and the new developments (as of 27 Oct 2025):
- Future Homes Standard (England) — status (as of 27 Oct 2025): The UK Government intends to publish the final FHS regulations in Autumn 2025, lay them before Parliament in December 2025, bring them into effect in December 2026, and apply a 12‑month transition to December 2027. From 2028, all newly commenced homes are expected to comply. FHS is designed to deliver zero‑carbon‑ready new dwellings and will be accompanied by the new Home Energy Model (HEM) for compliance. Timings and specific requirements therefore remain subject to final legislation and guidance.
- NIS2 (EU) — Operational security/risk‑management & incident reporting for essential/important entities: Examples of entities that may be in scope include managed service providers supporting critical sectors, operators of large data centres/digital infrastructure, and building‑technology SaaS providers above national size thresholds (scope depends on local transposition).
- Cyber Resilience Act (CRA) (EU) — Secure development & post‑market obligations for products with digital elements, in force 10 Dec 2024; phased obligations over ~3 years.
- RED Cybersecurity Delegated Regulation (EU) 2022/30: mandatory from 1 Aug 2025 for internet-connected radio equipment – covering cybersecurity essentials (network protection, privacy, anti-fraud).
- AI Act (EU) — Duties for AI systems (transparency/interpretability, logging, human oversight; phased) – Entered into force on 1 Aug 2024.
- GDPR — Personal data principles (lawful basis, minimisation, DPIA where needed).
- PSTI (UK) — Baseline device security (consumer connectable products): unique credentials, Vulnerability disclosure (VDP), and update transparency.
- EU Data Act: applies from 12 Sep 2025 (phased) with device-data access/sharing rights affecting IoT business models.
- ETSI EN 303 645 1.3 (2024-09): latest consumer-IoT security baseline; IASME aligns to it.
Cybersecurity Considerations
The proliferation of IoT devices has exponentially increased potential cybersecurity risks. Both UK and EU regulations emphasise:
- Secure device design
- Regular security updates
- Transparent vulnerability reporting
- Protection of personal data
- Minimising attack surfaces
For example, this typically entails:
- Unique‑per‑device credentials or forced credential change on first use.
- Signed OTA firmware updates with rollback and update‑support period declared.
- Coordinated vulnerability disclosure (e.g., security.txt) with a triage
- Asset inventory and Software Bill of Materials (SBOM) handling for third‑party components.
- Least‑privilege identities/keys and network segmentation at gateways
- Centralised logging, retention, and incident‑response playbooks with drills
Competitive Advantages of Compliance
Manufacturers and building operators who proactively embrace these regulatory frameworks can help themselves to:
- Reduce operational costs.
- Enhance building asset values.
- Access green building certifications
- Potentially earn revenue through grid services
- Differentiate themselves in the market.
- Reduce business risk exposure.
Technological Solutions and Innovations
Edge Computing and Privacy
To address privacy concerns, many IoT solutions are transitioning to edge computing architectures. This approach, favouring edge processing and GDPR data minimisation (Art. 5(1)(c)) to reduce personal-data flows in smart-building analytics helps mitigate risk, but also require secure and critical connectivity to ensure these nodes remain operational and able to:
- Process data locally securely and accurately
- Minimise external data transmission, while still sending and receiving critical updates securely.
- Align with GDPR’s data minimisation principles while maintaining operational effectiveness.
- Reduce latency in critical building systems while ensuring wider system synchronisation and appropriate intelligence gathering.
Artificial Intelligence
Transparency/interpretability, logging/record-keeping, and human oversight (AI Act Arts. 12–15)
The EU AI Act introduces requirements for transparency/interpretability, logging/record‑keeping, and human oversight for high‑risk systems (AI Act Arts. 12–15). In smart buildings, this means:
- Developing interpretable machine learning models
- Providing clear explanations for automated decisions
- Maintaining comprehensive decision logs
- Enabling human oversight of AI systems
Certification and Verification
Third-party certifications are emerging as crucial tools for demonstrating compliance. For instance, IoT Cyber certification offers manufacturers a structured path to meet regulatory requirements, with multiple levels of assurance.
Future Outlook
Both the UK and EU are positioning themselves as leaders in creating human-centric, secure IoT ecosystems. The regulations represent a balanced approach that:
- Encourages technological innovation.
- Protects consumer rights.
- Supports broader sustainability goals.
- Creates frameworks for responsible digital transformation.
Conclusion
The intersection of IoT, smart buildings, and regulation represents a critical frontier in technological development. By establishing clear guidelines and security standards, the UK and EU are not just mitigating risks but actively shaping a more secure, efficient, and user-friendly technological landscape.
The smart‑building opportunity now hinges on getting security, privacy, and reliability right. With PSTI in force, CRA/RED phasing in, and the AI Act timelines set, leaders should.
- declare and deliver a security‑update support period,
- align device and cloud controls to ETSI EN 303 645,
- minimise personal data via edge processing and DPIA where needed,
and
- track national guidance quarterly as CRA/RED mature.
Taking these steps turns compliance into a competitive edge—shortening procurement cycles and de‑risking large‑scale deployments.
As we move forward, continued collaboration between policymakers, technology developers, and certification bodies will be essential in refining these frameworks and ensuring they remain adaptive to emerging technological challenges.
Key Takeaways
- Regulatory compliance is becoming a competitive differentiator.
- Privacy and security are paramount in IoT development.
- Smart building technologies offer significant energy efficiency potential.
- Certification and transparent practices build consumer trust.
Implementation Challenges for Manufacturers and Integrators
| Control / Action | What good looks like | Evidence |
| Security‑update support period | ≥5 years declared; process owned; rollback plan | Datasheet + signed firmware manifest |
| Vulnerability disclosure policy (VDP) | security.txt + 48h triage commitment | VDP URL + ticketing workflow |
| EN 303 645 alignment | Mapped controls; optional external verification | Control matrix + certificate |
| Edge data minimisation | On‑device analytics; no raw personal data off‑device | DPIA + data‑flow diagram |
| Incident logging & response | Centralised logs; playbooks; notification plan | IR plan + sample runbook |
A Case example: Office retrofit (BMS + sensors)
To provide a real world insight: a 12‑storey office replacing fixed schedules with occupancy‑driven ventilation/lighting is considered:
If properly and securely implemented, likely outcomes would not only be HVAC runtime reductions, but also faster procurement sign‑offs and deployments due to regulatory alignment already being in place prior to scaled deployments.
For such projects, it is therefore important to plan for and implement the following:
- Set and disclose a defined security‑update support period (PSTI) and ensure update infrastructure (signing, hosting) is reliable for that period.
- Publish and operate a vulnerability disclosure policy (VDP); integrate intake, triage, fix and coordinated disclosure into product lifecycle.
- Map product controls to ETSI EN 303 645; consider third‑party certification (e.g., Cyber Baseline/Assurance) for buyer assurance.
- Prepare for CRA obligations (secure development, vulnerability handling, security updates, conformity assessment, and CE marking changes).
- For wireless/IoT devices, plan for RED Delegated Regulation 2022/30 applicability from 1 Aug 2025 (network protection, privacy, anti‑fraud).
- Security architecture: device identity/attestation, secure boot, encrypted comms, least‑privilege, hardening, and SBOM management.
- Data protection by design/default: minimise personal data, prefer on‑device or edge processing, and document purposes/retention.
- Post‑market surveillance and incident response: monitoring, logging, update rollback, and customer notification processes.
- Supply‑chain due diligence for components, cloud services, and third‑party libraries; vendor SLAs aligned to declared support period.
Ethical Considerations: Privacy, Consent, and Transparency
- Use privacy‑by‑design defaults: collect the minimum personal data; anonymise/aggregate where possible; edge processing for occupancy analytics.
- Be explicit about purposes, retention, and data sharing; provide layered notices in clear language (transparency).
- Offer meaningful user controls and opt‑outs; avoid deceptive or misleading patterns in consent flows for workplace/residential contexts.
- Assess impacts via DPIA for high‑risk sensing/AI (e.g., biometrics, large‑scale tracking, innovative tech uses).
- Ensure human oversight for high‑risk AI in BMS/property technology (monitorability, intervention capability, logging).
International Comparisons
- United States: NISTIR 8259/8259A baselines for IoT device cybersecurity capabilities; California SB‑327 bans universal default passwords. California’s SB-327 requires ‘reasonable security’ and effectively eliminates universal defaults by mandating unique credentials per device or forcing a new credential at first use.
- Singapore: Cybersecurity Labelling Scheme (CLS) rates consumer IoT security across levels; growing mutual recognition with partner countries.
Glossary
- AI Act: European Union legislation providing governance for artificial intelligence systems, establishing transparency, logging, and oversight requirements for high-risk AI technologies.
- BMS (Building Management System): Integrated computer-based control system that monitors and manages building technical equipment like HVAC, lighting, and security systems.
- Cyber Resilience Act (CRA): EU regulation (2024/2847) addressing cybersecurity for products with digital elements, with phased obligations through 2027.
- DPIA (Data Protection Impact Assessment): Systematic process to identify and minimize data protection risks in high-risk processing activities.
- EPBD (Energy Performance of Buildings Directive): EU regulatory framework promoting smart technologies and energy efficiency in buildings.
- GDPR (General Data Protection Regulation): Comprehensive EU data privacy and protection regulation.
- GPAI (General Purpose AI): Broadly applicable AI systems with multiple potential use cases.
- IoT (Internet of Things): Network of interconnected physical devices or assets that collect and exchange data.
- NIS2 Directive: EU cybersecurity legislation setting obligations for essential and important entities.
- PSTI Act (Product Security and Telecommunications Infrastructure Act): UK legislation mandating security requirements for consumer-connected devices.
- RED (Radio Equipment Directive): EU regulation addressing cybersecurity for internet-connected radio equipment.
- SBOM (Software Bill of Materials): Comprehensive inventory of software components used in a product.
- Transparency Duties: Regulatory requirements for clear disclosure of AI system operations, decision-making processes, and potential risks.
References
- UK Government — PSTI regime overview (came into effect 29 Apr 2024): https://www.gov.uk/government/publications/the-uk-product-security-and-telecommunications-infrastructure-product-security-regime
- UK SI 2023/1007 — PSTI Security Requirements Regs (commencement 29 Apr 2024): https://www.legislation.gov.uk/uksi/2023/1007/contents/made
- EU AI Act implementation timelines (overview): https://artificialintelligenceact.eu/implementation-timeline/
- EPBD recast — Official Journal entry (8 May 2024; in force 28 May 2024): https://eur-lex.europa.eu/eli/dir/2024/1275/oj/eng
- EPBD timeline summary (transposition by 29 May 2026): https://www.crosscert.eu/fileadmin/user_upload/1.1_EPBD_adopted_by_EP_and_Council_-_Next_generation_EPCs.pdf
- NIS2 — Commission overview (transpose by 17 Oct 2024): https://digital-strategy.ec.europa.eu/en/library/nis2-commission-implementing-regulation-critical-entities-and-networks
- Cyber Resilience Act — Regulation (EU) 2024/2847 (in force 10 Dec 2024; phased obligations): https://eur-lex.europa.eu/eli/reg/2024/2847/oj/eng
- ETSI EN 303 645 (consumer IoT cybersecurity) standard: https://www.etsi.org/deliver/etsi_en/303600_303699/303645/03.01.03_60/en_303645v030103p.pdf
- IASME IoT Cyber scheme (aligns with PSTI/ETSI EN 303 645): https://iasme.co.uk/iasme-iot-cyber/
- PNNL / DOE — Commercial building controls energy‑savings potential (~29%): https://www.pnnl.gov/news-media/cut-us-commercial-building-energy-use-29-widespread-controls
- ACEEE — Smart buildings energy savings discussion: https://www.aceee.org/sites/default/files/publications/researchreports/a1701.pdf
- Europe smart building market estimates — SkyQuest/Fortune BI (18.59 bn by 2030): https://www.skyquestt.com/report/europe-smart-building-market/market-size (retrieved 27 Oct 2025)
- Europe smart building market estimates — Fortune Business Insights (26.4 bn by 2032): https://www.fortunebusinessinsights.com/europe-smart-building-market-105128 (retrieved 27 Oct 2025)
- GDPR Article 5(1)(c) — Data minimisation: https://gdpr-info.eu/art-5-gdpr/
- ICO guidance — DPIA: https://ico.org.uk/for-organisations/uk-gdpr-guidance-and-resources/accountability-and-governance/data-protection-impact-assessments-dpias/
- Singapore CSA — Cybersecurity Labelling Scheme (CLS): https://www.csa.gov.sg/our-programmes/certification-and-labelling-schemes/cybersecurity-labelling-scheme/about/
- NISTIR 8259A — IoT device cybersecurity capability core baseline: https://csrc.nist.gov/pubs/ir/8259/a/final
- California SB‑327 default‑password law overview: https://natlawreview.com/article/iot-manufacturers-what-you-need-to-know-about-california-s-iot-law
EU/UK Regulatory Timeline